The OSI Model: Understanding the 7-layer Network Model
The OSI model is a commonly used model for referencing the different levels involved in networking. While it’s not a solution or implementable rule in itself, it’s a concept used in industry that makes networking more tangible. When building, changing, fixing, or securing a network, it helps to break everything down based on what is happening at a given layer.
The seven layers start at the bottom with layer 1 and end at the top with layer 7.
Let’s take a look at the model.
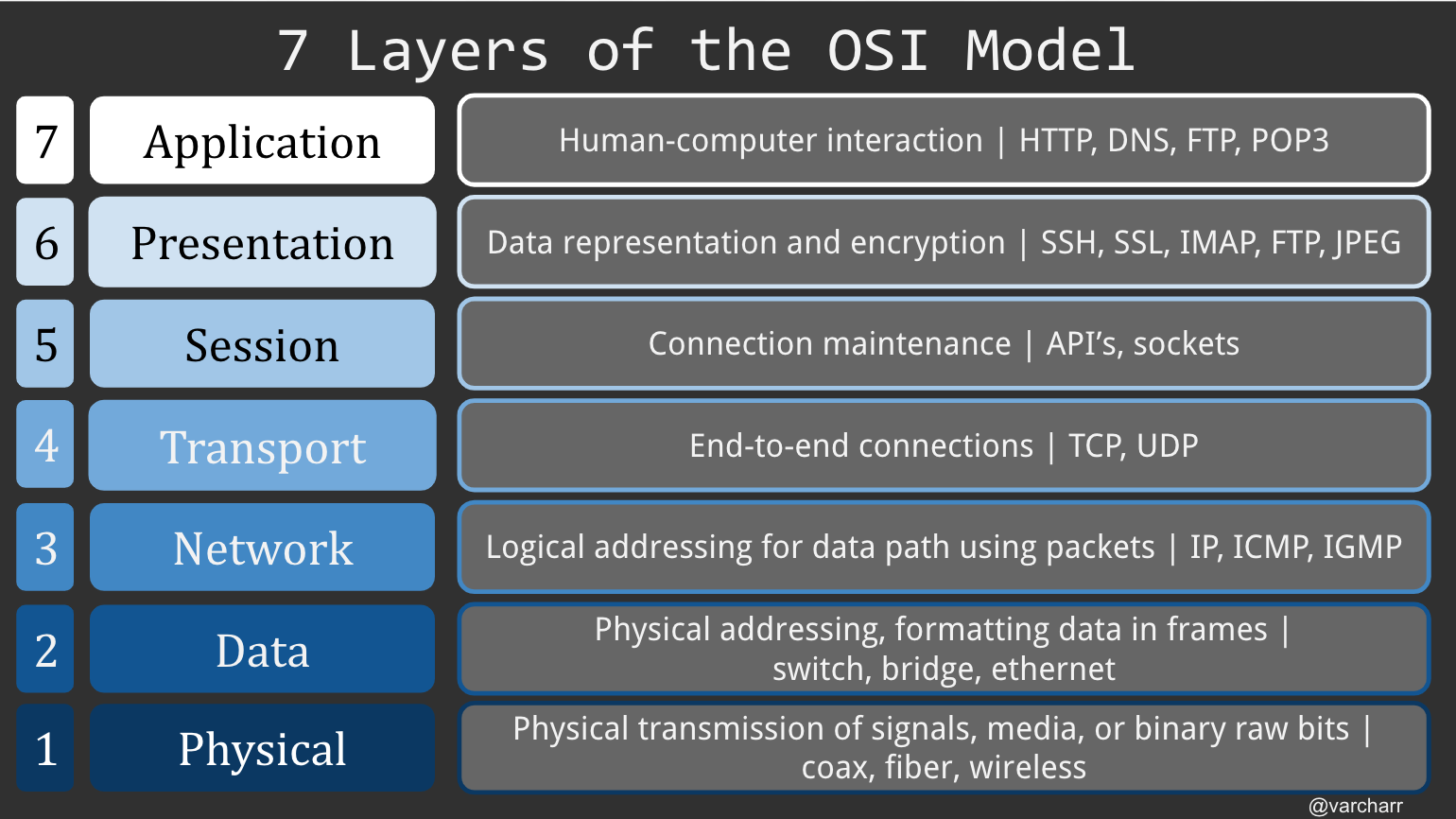
If we start at layer one, the physical layer, we see that we’re talking about the lowest level type of data- raw bits. Electrical requirements such as voltage and bit layouts are relevant here. If something were to go wrong at this level, it would mean needing to replace the physical means, like a cable or RF (Radio Frequency) link, by which the bits are traveling.
At layer two, known as either the data or data link layer, physical addressing occurs with MAC (Media Access Control) addresses. MAC addresses are unique identifiers for hosts on a network. Endpoints can communicate directly with each other using MAC addresses.
Layer three is the network, or routing, layer. Here, endpoints communicate using IP (Internet Protocol). This layer is responsible for packets successfully traversing through series of networks and routers by providing conducive frame sizes. Should packets be too large to move through certain parts of a network, they can be fragmented.
Layer four, the transport layer, gets more specific about how and where data is going to be sent and shared between endpoints. The most common protocols used here are TCP and UDP. This layer is considered as being in charge of reliability due to how these protocols work. Depending on the use case, UDP can be used for broadcasting and streaming to provide a constant flow of data, whereas TCP will provide ensured receipt of data as well as receive packets in order. For more information on TCP and UDP, check out my blog post comparing the two.
At layer five, the session layer, the connections enabled with protocols such as TCP are established, maintained, and closed for their respective sessions. A session is simply an open, established flow of data between two endpoints. This layer also includes port control.
Layer six, the presentation layer, deals with two main things, data representation, or syntax, and encryption. Data is either prepared to be used (or presented) by the application layer, or being translated from an application layer format to a network layer format. That’s why we see both a protocol like JPEG included here, as well as SSH and FTP. Because the presentation layer is somewhat intertwined with the application layer, there are some shared protocols between the two (e.g. FTP).
Finally, at layer seven we get to the application layer. This is the layer at which a user interacts, for example checking email or searching the web.
And there we have it! As you can see, the OSI model covers the whole suite of networking roles and protocols, down from the bit level up to the human interface level.